Fontys S4
Network sniffing and spoofing
I will show 2 little demos as a proof of concept.
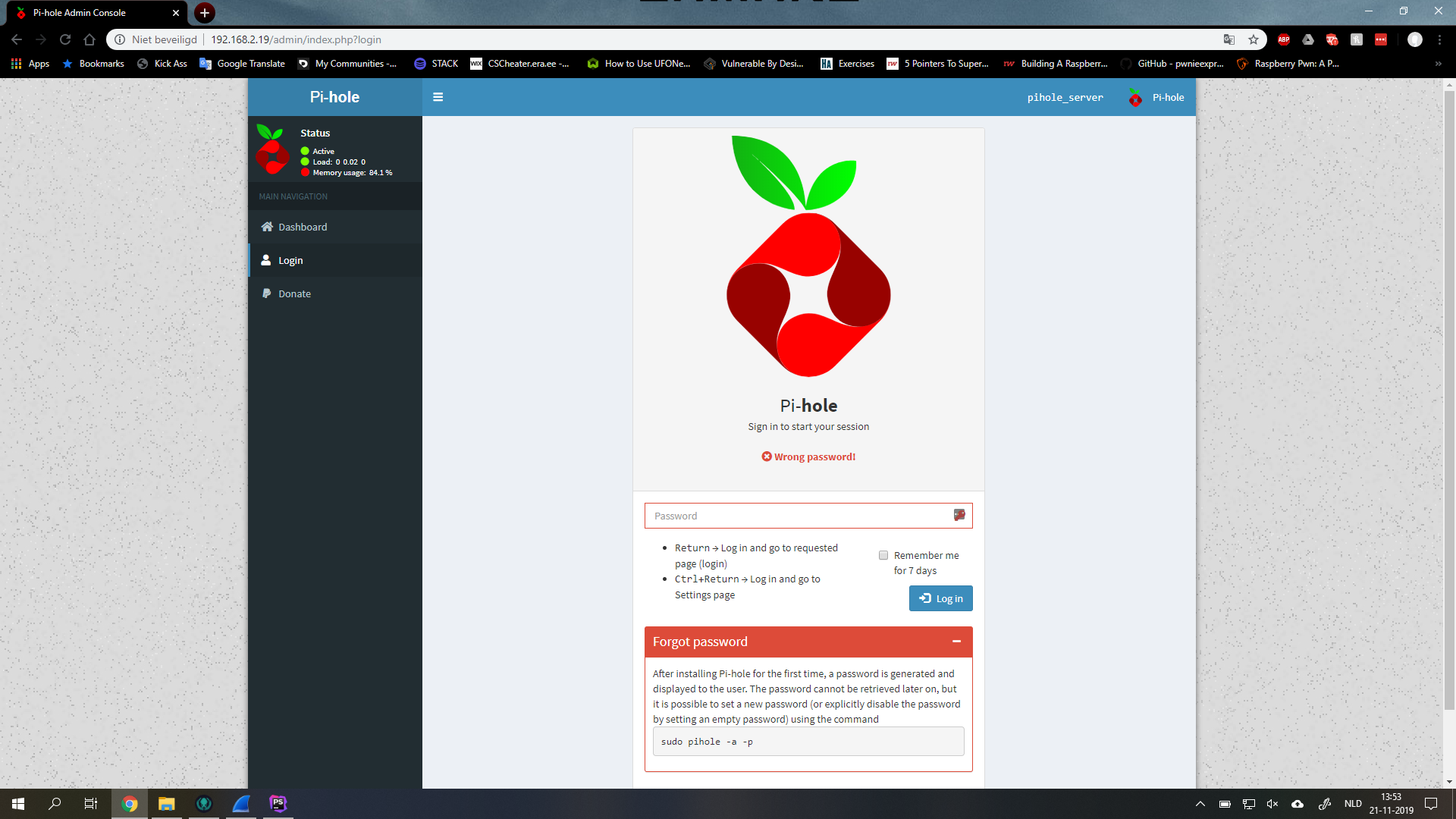
I have a "pi-hole" server running on my network that acts as my home dns server. It has a login screen for a dashboard with statistics but it is not HTTPS secured. So I tried catching the password with Wireshark while logging in.
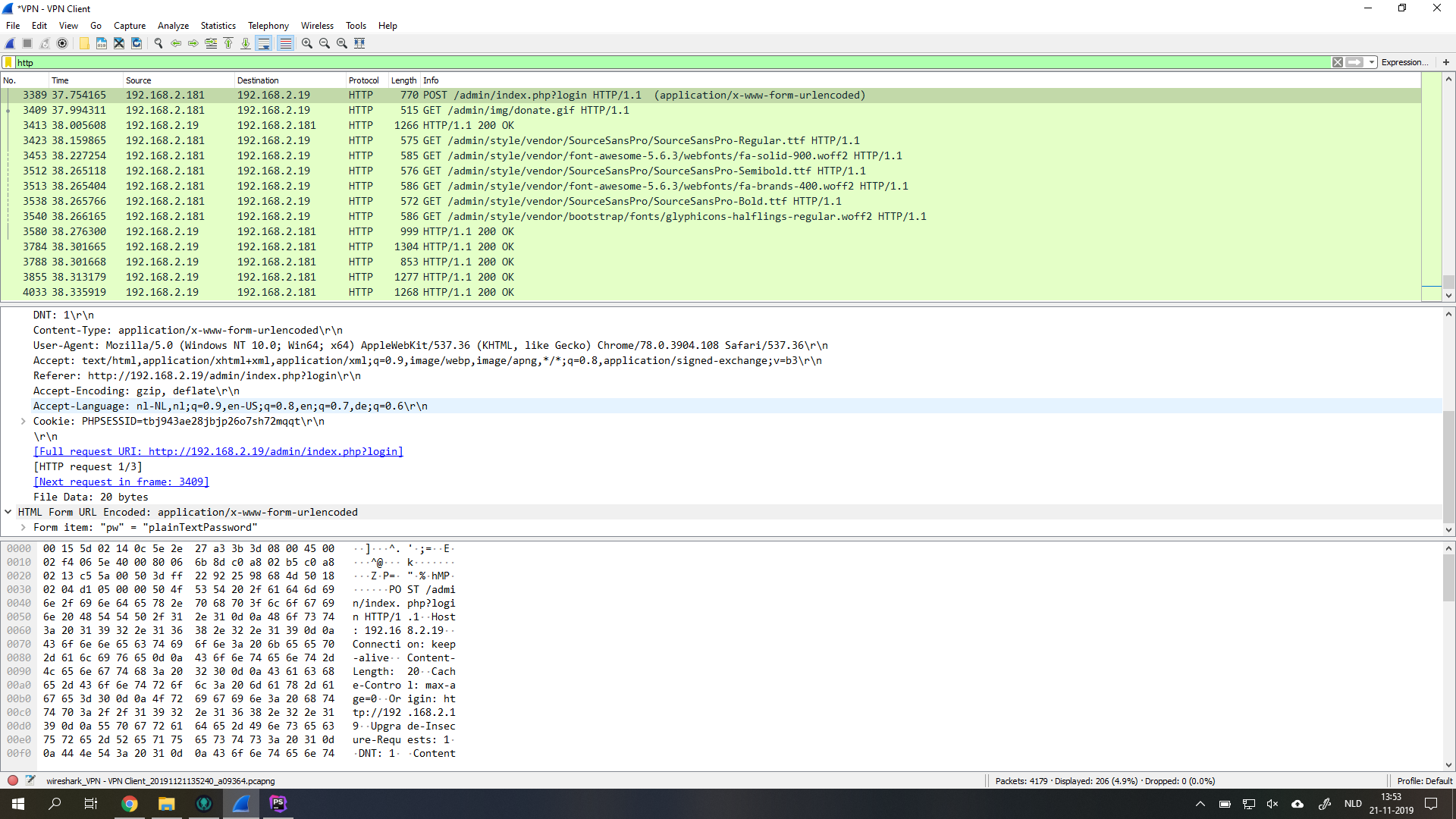
When I filter Wireshark to only HTTP and logged in in te website I can see my IP and the website's IP. When I open the packet and took a look what's inside, you can see the form post with password in plain text. Now this website doesn't hash the password so I can see the password in plain text, otherwise I would have seen a hash which I had to decrypt to get the password.
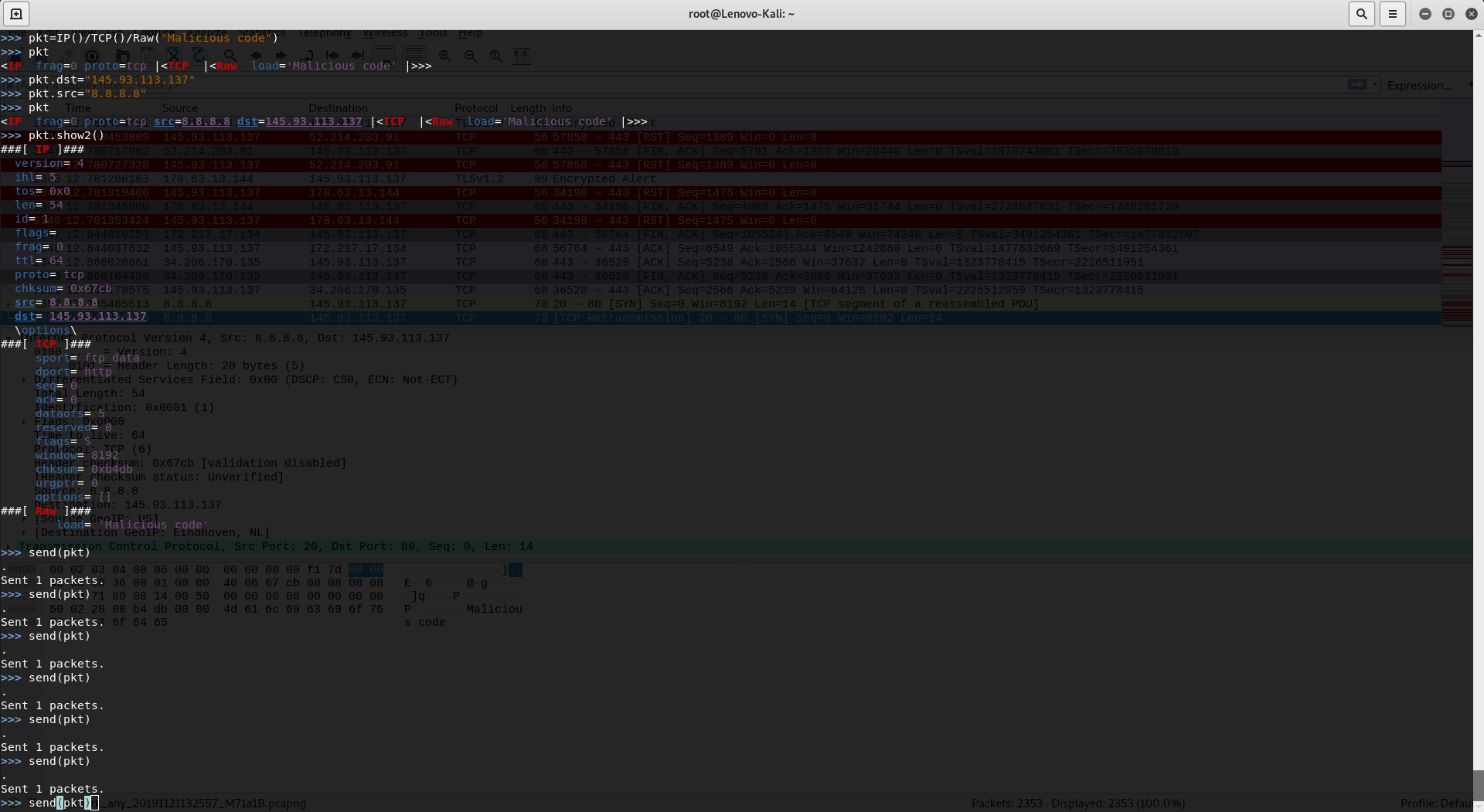
I created a fake IPV4 packet using "scapy". I made it so that it looks like the packet is coming from google, but It's actually from me and I put my malicious code in it.
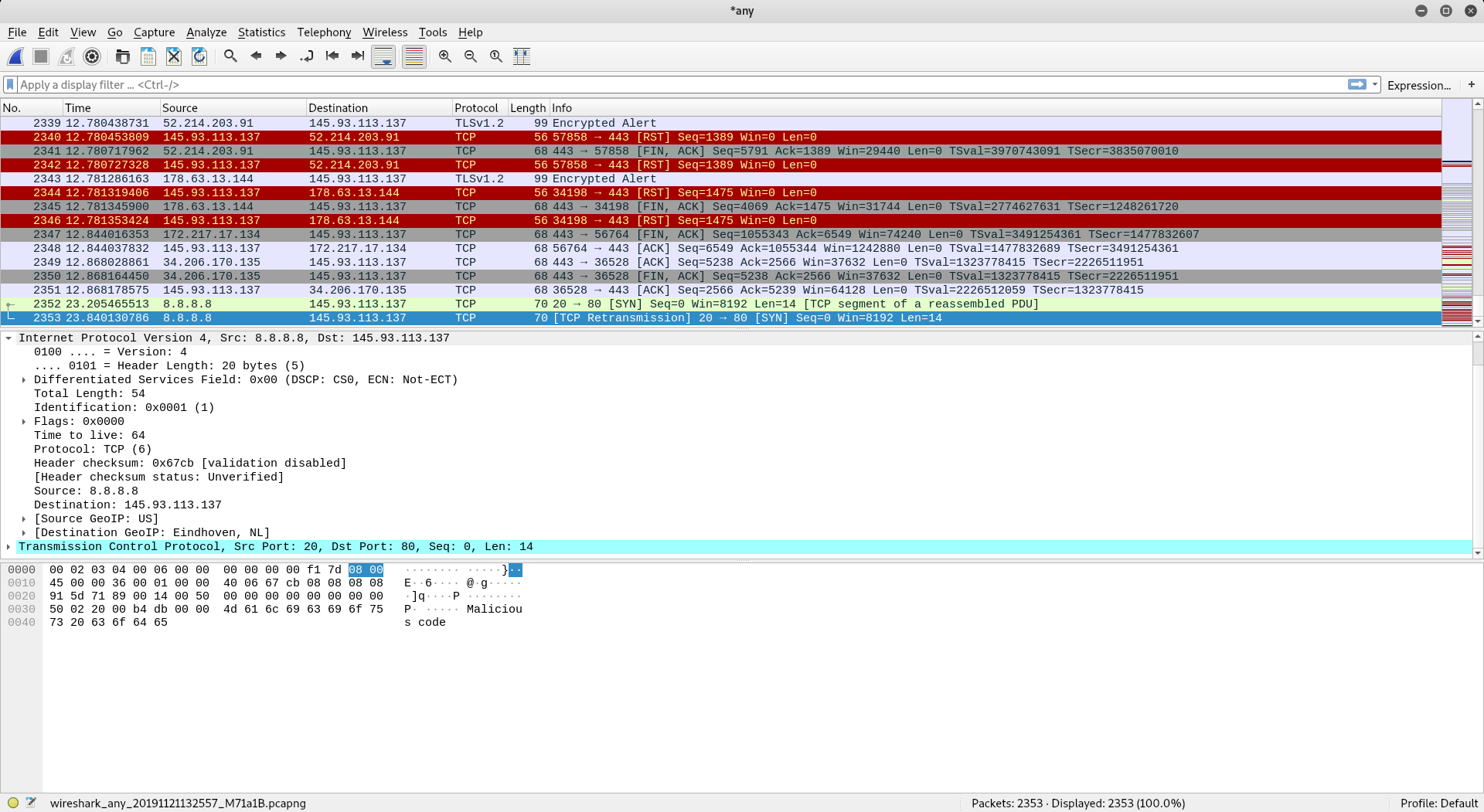
I captured the packet with Wireshark and as you can see the source address is google, but when you look in the raw my malicious code is in there.
- Date: November 2019
- Client: Fontys
- Category: Network sniffing and spoofing