Fontys S4
Password cracking
Now I'm going to show to basics of password cracking.
There are a few main ways to crack passwords
- Brute forcing
- Dictionary attacks
- Rainbow tables
Brute forcing is the most basic way to crack a password, it just tries every possible combination of letters. It has a few pros and some big cons.
Brute forcing is rarely used these days just for the simple reason that cracking a modern encrypted password would take more then a lifetime. It also costs a lot of computing power because it generates the hashes on the fly and there are a lot of hashes to generate and try. The pro is though that it doesn't use any storage space because it generates everything instead of getting them for a wordlist. Brute forcing could be an option when you know that the password that you're cracking isn't a existing word but rather a string of random numbers and letters. Even though brute forcing might be the only option in that case, you're probably better off finding another way to get the password.
Dictionary attacks are more sophisticated, it's way more efficient and faster but there a big con.
Dictionary attacks use a predefined list of words and generates hashes for them and then compare them to the hash you want to crack to see if any of them match. The pro is that this is way faster. The downside on the other hand is that if the password you want to crack isn't in the word list you have no chance of success. The dictionary attack could be extended by generating multiple versions of every word some with captitals some with random numbers after them etc. A dictionary attack could also be made very personal and tailored to the specifications of your target. For example adding the targets place of work or pet names to the list. Also if you want more chance of success you'll need a bigger word list and those can grow pretty fast costing thus a lot of storage space.
Rainbow tables are in essence a lot like dictionary attacks, but actually better.
Rainbow tables contain like a dictionary attack a wordlist. The difference is that the wordlist is already hashed and could contain all possible solutions making a look like a brute force. You could for instance create a rainbow table having every possible solution making it a bruto force but more efficient costing less time, or generate hashes for your dictionary attack wordlist which might be reusable costing you less time in the future. Rainbow tables do come with some downsides like it costs a lot of harddisk space, less then a dictionary attack of the same size because it uses lossless compression, but if you want a lot of possibilities it will still be a big file. The hash type like MD5 or SHA256 is static thus making it less versatile/useful when you don't know the encryption type. Same goes for the salt, a salt could be added to the list but it will make the file even bigger. A problem that you won't have with a dictionary attack or brute force because the hashes get generated in the fly.
A good way to make encrypted passwords harder to crack is by using a salt or a pepper. A salt is random data added to the password before it's hashed, and because it's different for every new password it gets stored alongside the password. This has a pro and a con. The pro is that the salt is different for every password meaning that if one password gets compromised the others are still save. The downside is though that if someone breaches the database he will know the salts for each password instantly. Now a pepper uses the same method to encrypt a password, it is random data and adds it to the password before it's hashed. But a pepper is static and is stored separately from the password hashes. Now this method has a pro and con as well. The pro is that if the database is breached the hacker won't know the pepper making cracking the passwords a lot harder. The con is that if he finds the pepper all the passwords are compromised, but to do that he might need to decompile the code and find the pepper, which is a lot harder than breaching the database most of the time.
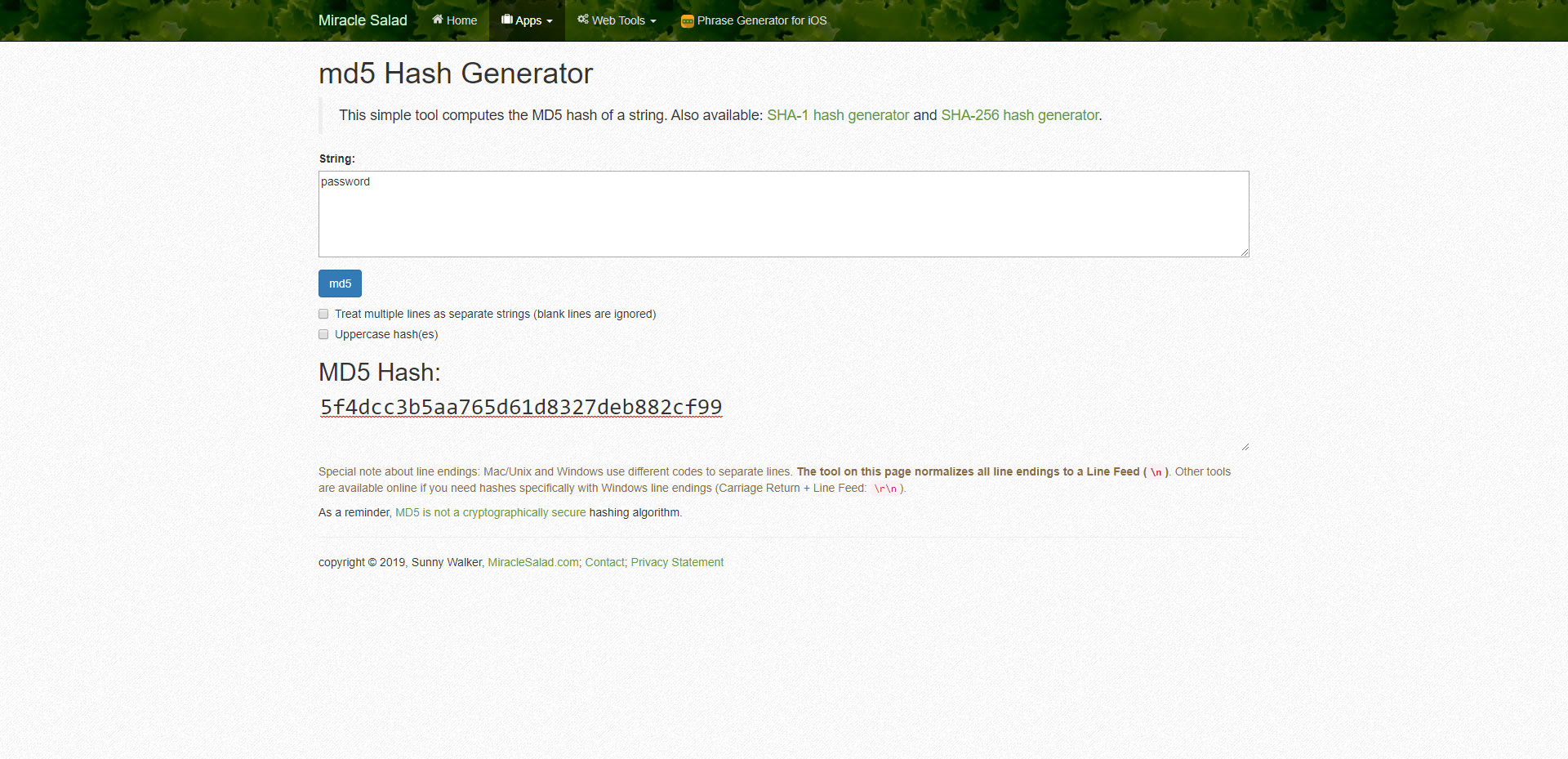
I created a small demonstration on hacking a simple MD5 hash. So I first of all created a hash for the string "password".
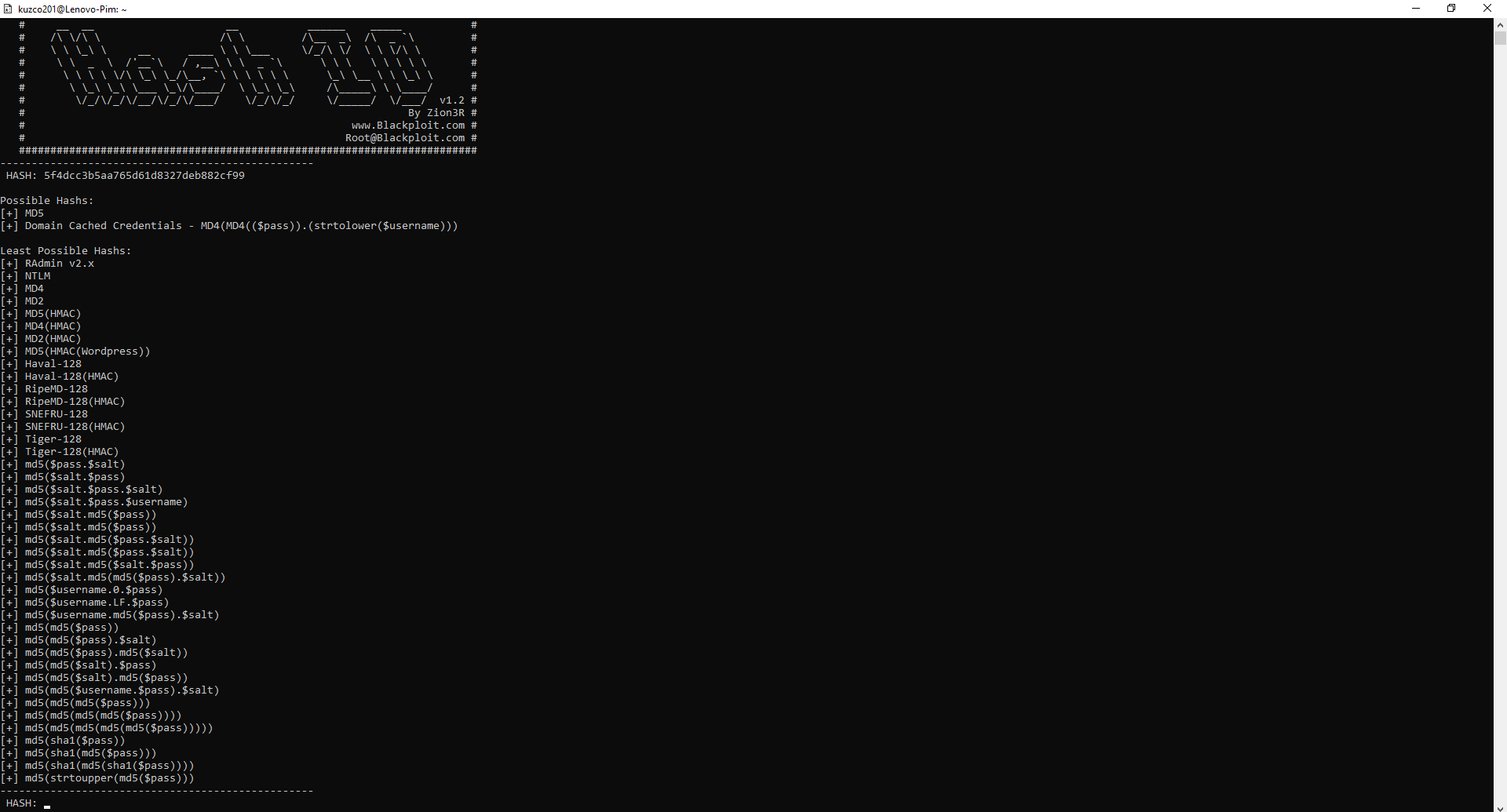
If I would have stole this hash from some database I might not know the hash type, which is important for me to know if I want to save time or use a rainbow table. So I ran "Hash-identifier" and gave it the hash. This gives me an idea what the hash type might be.

I placed the has in a file. In this case there's only one hash in there but in reality this list could contain all the hashes from a certain database.
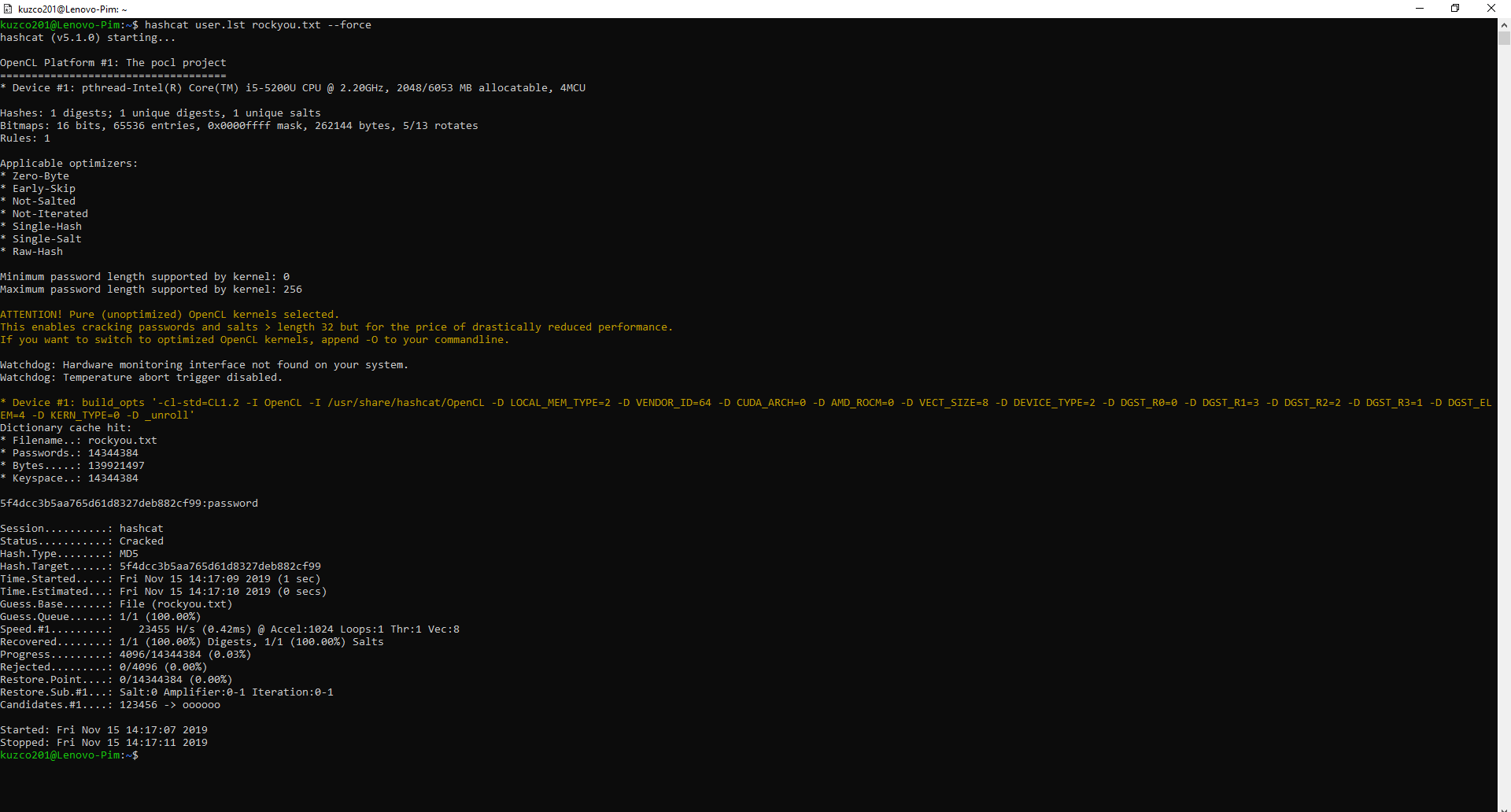
Now I used "Hashcat" to crack the password using a wordlist called "rockyou". This wordlist contains the most common password based on data breaches in the past. As you can see it cracked the password and it only took 1 second. Do mind that in this case the password was high up in the wordlist. The program only went through 0.03% of the entire wordlist, if the password was much lower in the list this would take a lot longer.
- Date: November 2019
- Client: Fontys
- Category: Password cracking