Fontys S4
Basic hacking process
First lets talk about the basic hacking process. This is a process most hackers will follow when conducting a hack, good or bad. Though good and bad use this process there is a key difference between the two.
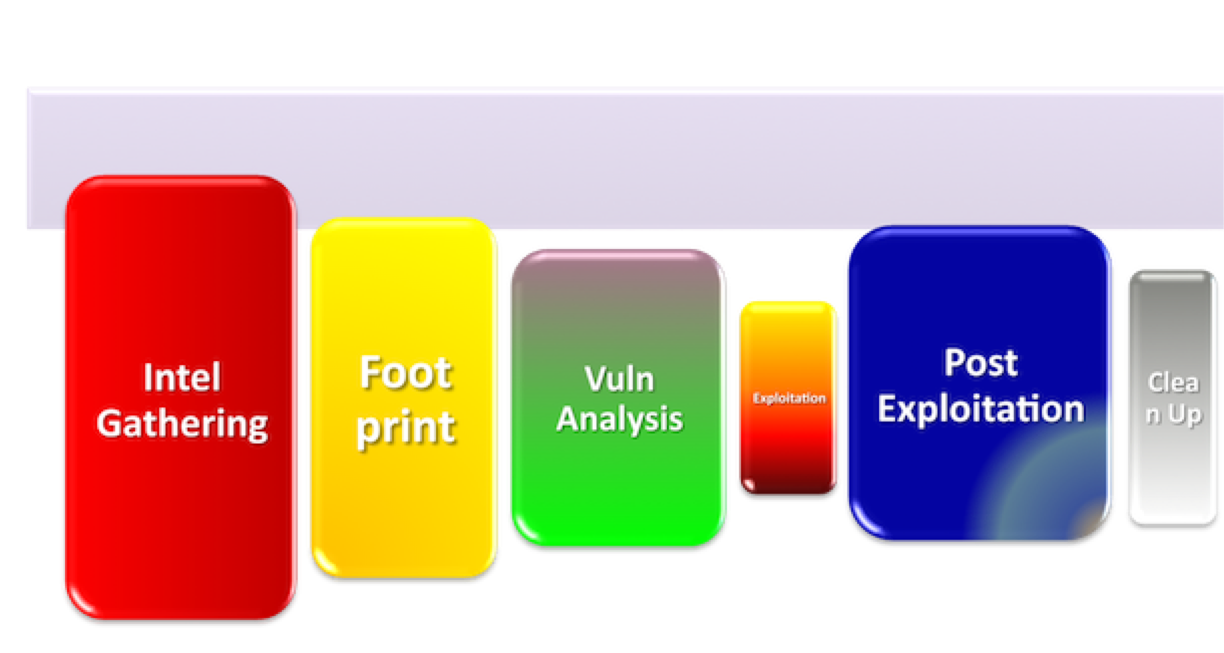
These are the basic hacking steps that are needed to conduct a good hack.
Intel Gathering
Intel gathering is the first step in the basic hacking process. In this step the hacker tries to gain as much information on his target as possible. He'll conduct for instance a OSINT, go to the physical location of his target and get a feel for the place and maybe even use social engineering to call his target and try to extract information.
Footprint
Now the hacker will conduct a network scan and try to gain as much information on the target's network as possible. He needs to find a foothold from which he can continue further, think about ip ranges, open ports, OS versions and important servers.
Vuln Analysis
The hacker will now look for any out of date software or operating systems to use exploits on. Whenever he'll find a software version he'll look if there's a CVE entry for that he could exploit. He might also use some automated tools to find common vulnerabilities for him. The hacker will also try any website for web vulnerabilities like SQL injection, command injection, CSRF and XSS.
Exploitation
Now is time for action. The hacker will use the information and vulnerabilities he found in the previous step to use his exploits. Thus gaining access to his target or the information he's after. Most ethical hackers/pentesters will stop after this step or not even do this step at all because it might result in destabilizing or shutting down the targets network.
Post Exploitation
This step and the following is more applicable to the bad actors out there. Here the hacker will extract the data he's after, edit some data, create new accounts and setup persistence for a backdoor so he can come back later without going through the same process again or have the risk of the target patching the vulnerability he used.
Clean Up
This step is very important for bad actors to not get caught. Here the hacker will try to remove all of his footsteps like logs. Therefore the police or target will not be able to track him down or even know what he did in the first place.
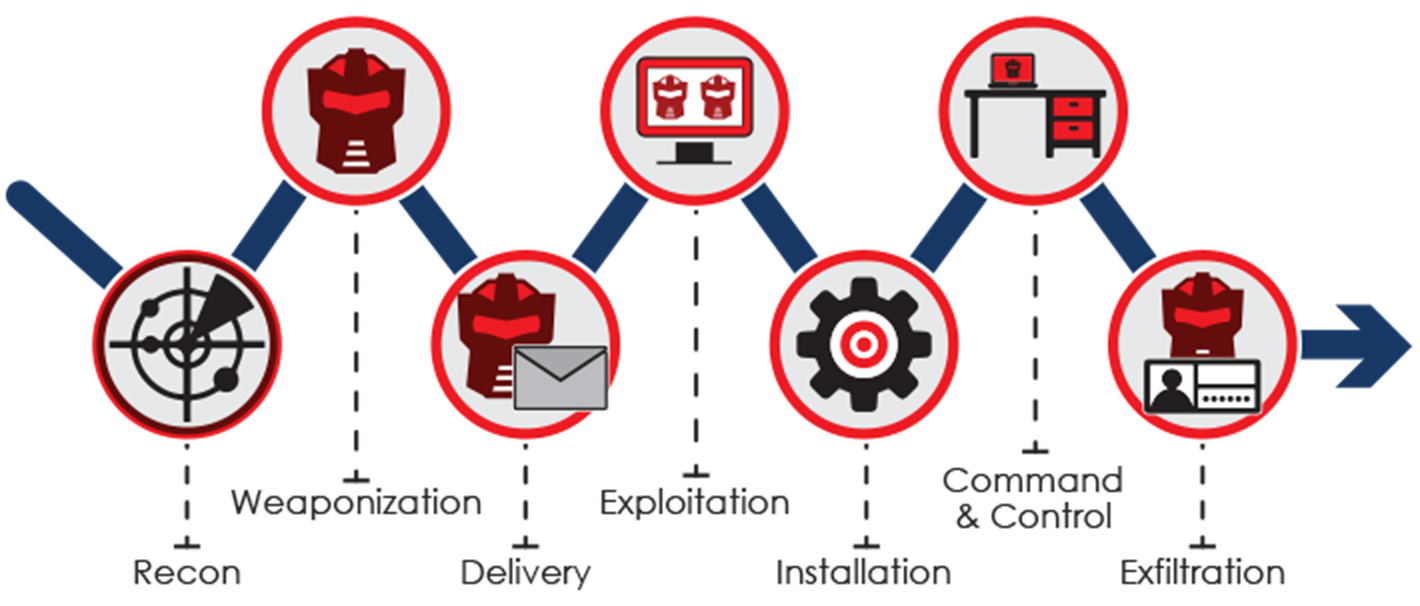
Now this is the cyber kill chain even though it's comparable to the basic hacking process there are some differences.
Reconnaissance
Here the hacker will conduct recon comparable to the intel gathering stage in the basic hacking process.
Weaponization
In this step the hacker is already creating a payload with an exploit to attack his target. It is notable that in the cyber killchain they skip the footprint and vuln analysis stages.
Delivery
Now the payload is to be delivered to the target this can be done by phising email, rubber ducky and so on. This stage is also not present in the basic hacking process, there it's more part of the exploitation stage.
Exploitation
When the payload is delivered the hacker will activate his attack.
Installation
In this stage the hacker will install for example malware to create persistence for a backdoor or to act more stealthy. This would happen in the post exploitation stage in the basic hacking process.
Command & Control
Now the installed malware will call back to the command and control system and give the hacker control of the hacked system. This can be both part of the exploitation and post exploitation stage in the basic hacking process.
Actions on Objectives
Here the hacker will do whatever his intentions were.
The minimal requirements for a good pentest contract and pentest report
In a good pentest contract there should be a clearly defined scope and procedures in case of emergency. The contract should also include a confidentiality agreement. The pentest report should include the scope and goal of the project with the findings and how it was done. It should be explained very carefully and readable for people that weren't aware of the project. The most important thing is ofcourse the advice to give to the company, this way they'll be able to fix any security leaks and the pentest was a success.
- Date: January 2020
- Client: Fontys
- Category: Basic hacking process