Fontys S7
Pen-testing methodologies
The standard and most popular pentest methodology is the Lockheed Martin cyber killchain. It's a basic process that explains the order of action a criminal hacker would follow. Thus also making it a viable ethical hacker methodology.

Knowing what step a attacker is taking or needs to take is good to know. But it's also good to know how to mitigate or prevent each step of the cyber killchain.
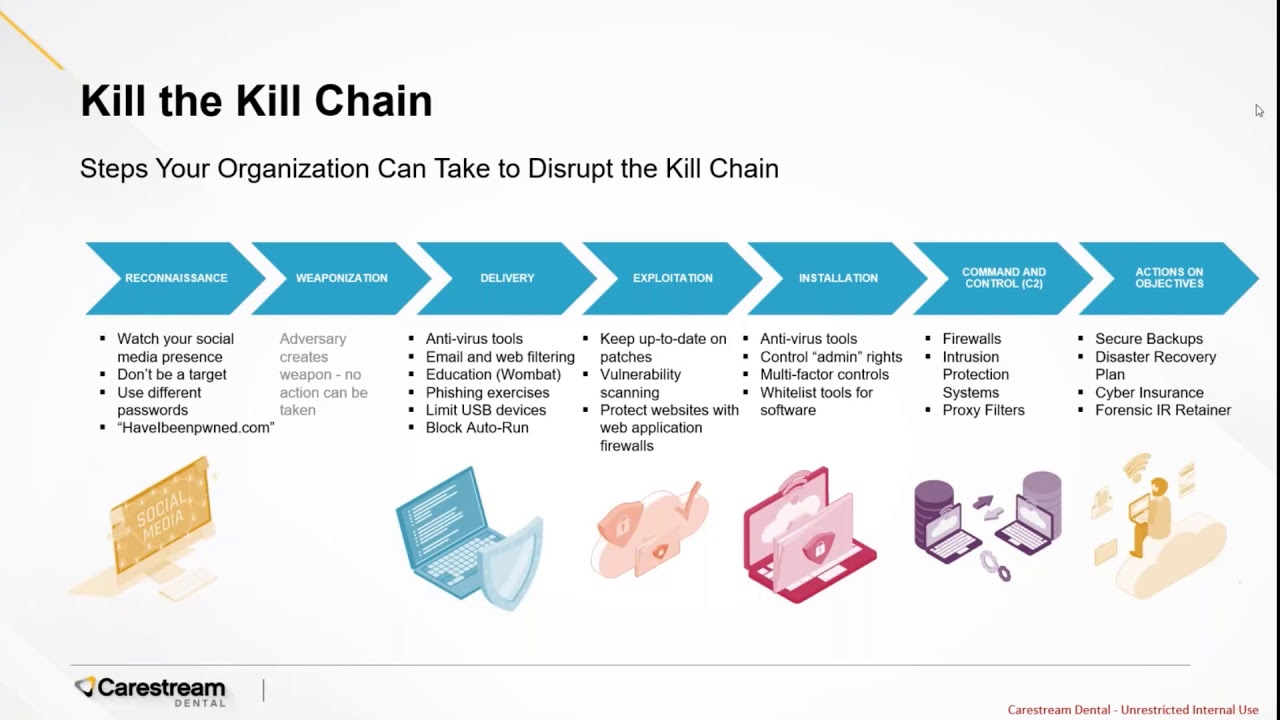
Other than the Lockheed Martin cyber killchain there are a few other frameworks/methodologies, like the well-known OWASP.
- OSSTMM (Open Source Security Testing Methodology Manual)
- OWASP (Open Web Application Security Project)
- NIST (The National Institute of Standards and Technology)
- PTES (Penetration Testing Methodologies and Standards)
- ISSAF (Information System Security Assessment Framework)
OSSTMM is a peer-reviewed security assessment standard for testing and auditing systems and providing them with a risk score
OWASP is used as a methodology to pentest websites and web applications.
NIST is a very strict standard and they promote themselves as functionality driven. They mainly focus on helping federal agencies comply with regulations.
PTES is a structured approach to pentesting and looks a lot like the Lockheed Martin cyber killchain.
ISSAF is a pentesting methodology where the pentester imitates a hacker. This also looks a lot like the Lockheed Martin cyber killchain.
Apart from all these methodologies there's another well known entity known by not only red teamers but also well-known by the blue teamers. This framework is known as the Mitre ATT&CK Framework this framework contains almost every possible way to attack a network or machine.
I've used the Mitre ATT&CK framework a lot when monitoring the SOC in my home network. Wazuh automatically categorizes the incoming alert in the Mitre ATT&CK framework. On the opposite side from te red teamer perspective I've used OWASP and the Lockheed Martin cyber killchain a lot. Mostly when performing pentests but also when cracking machines on Hackthebox and when participating in CTF events.
- Date: September 2021
- Client: Fontys
- Category: Research Skill