Fontys S3
IDS/IPS
I implemented Suricata as my IPS, I thought it would be the best option because they say it's more advanced and newer. Below you can see some prove of the implementation and some results I came across.
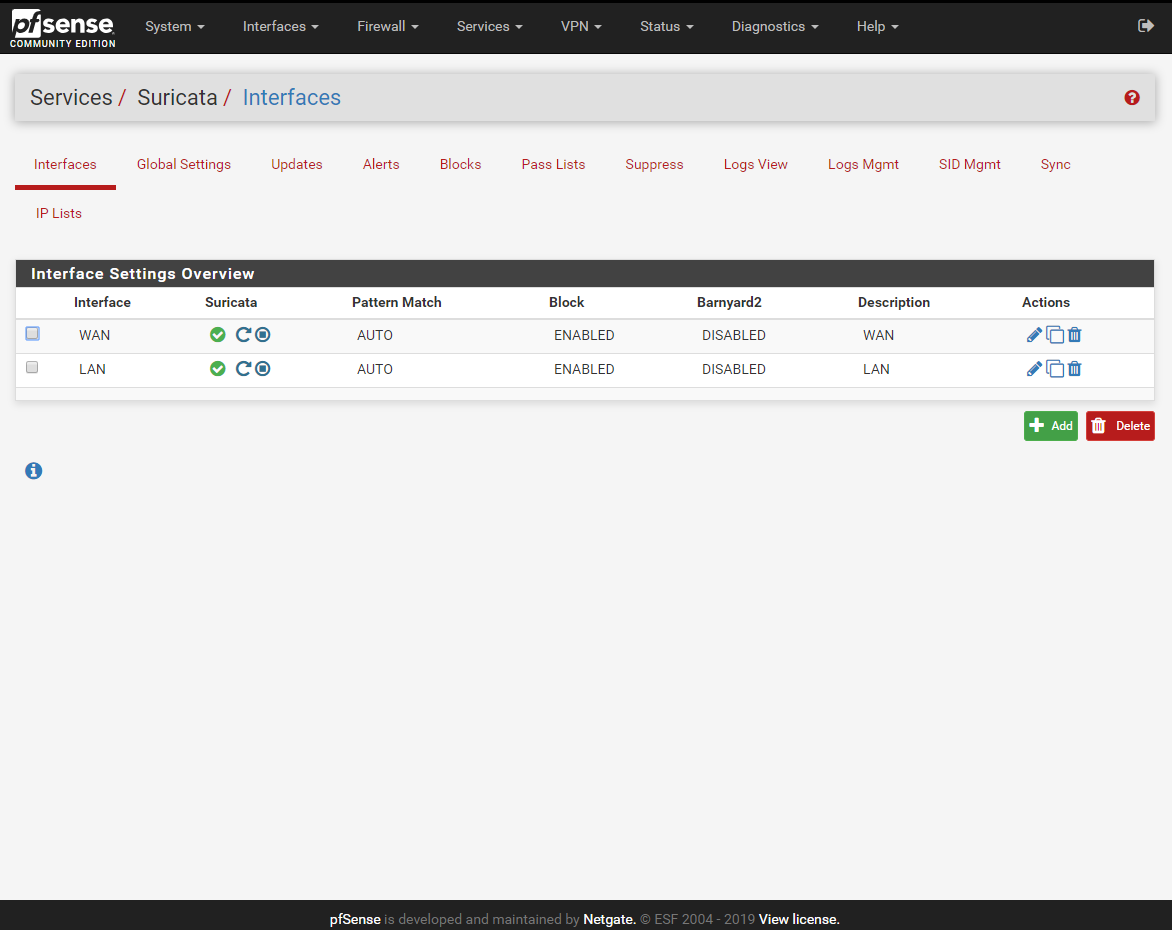
I configured the IPS to monitor the WAN and LAN interface for now but I'm planning to configure it to the Employee VLAN as well. This will protect the company for any potential threats from the inside.
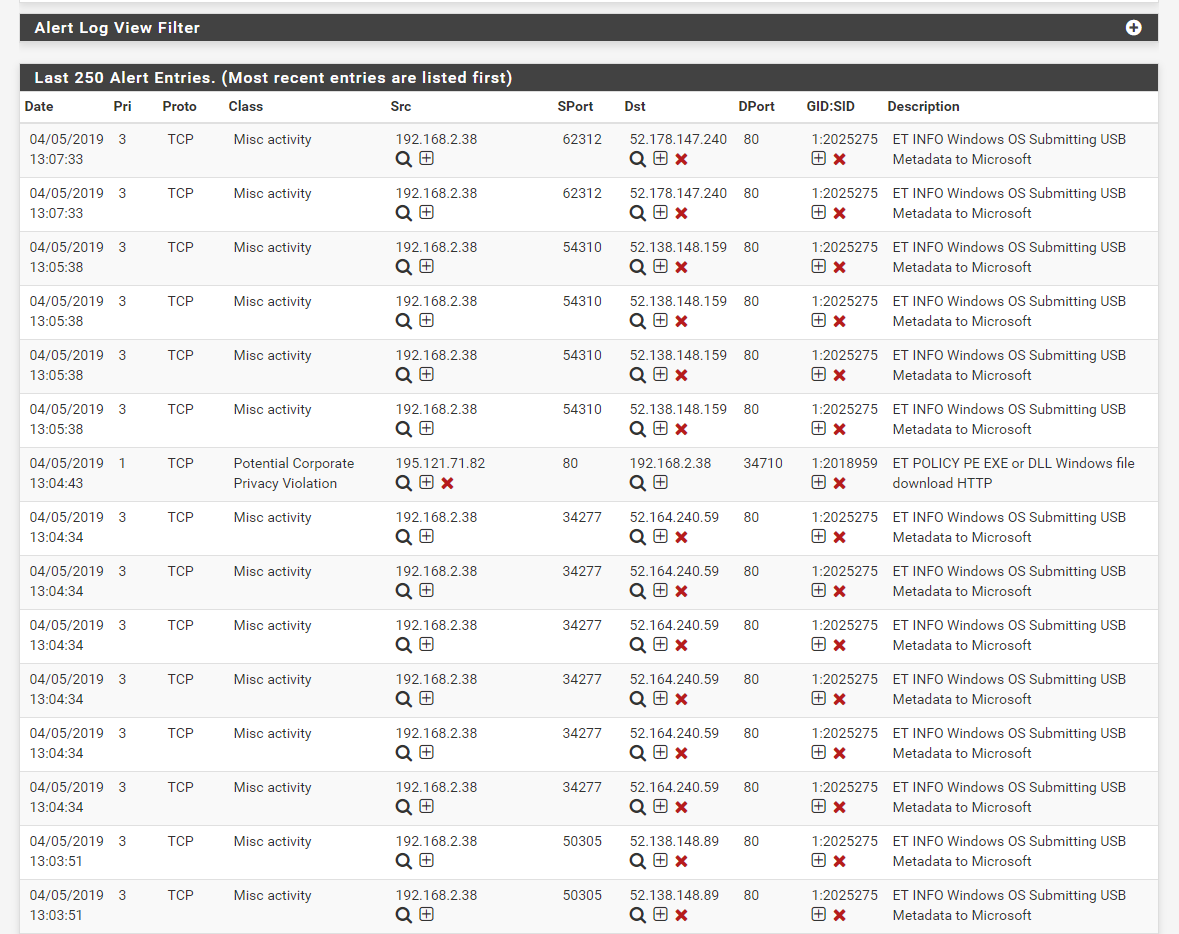
I tested the IPS with a website called Wicar. On this website you can run malicious code and test you network without it being an actual threat or risk.
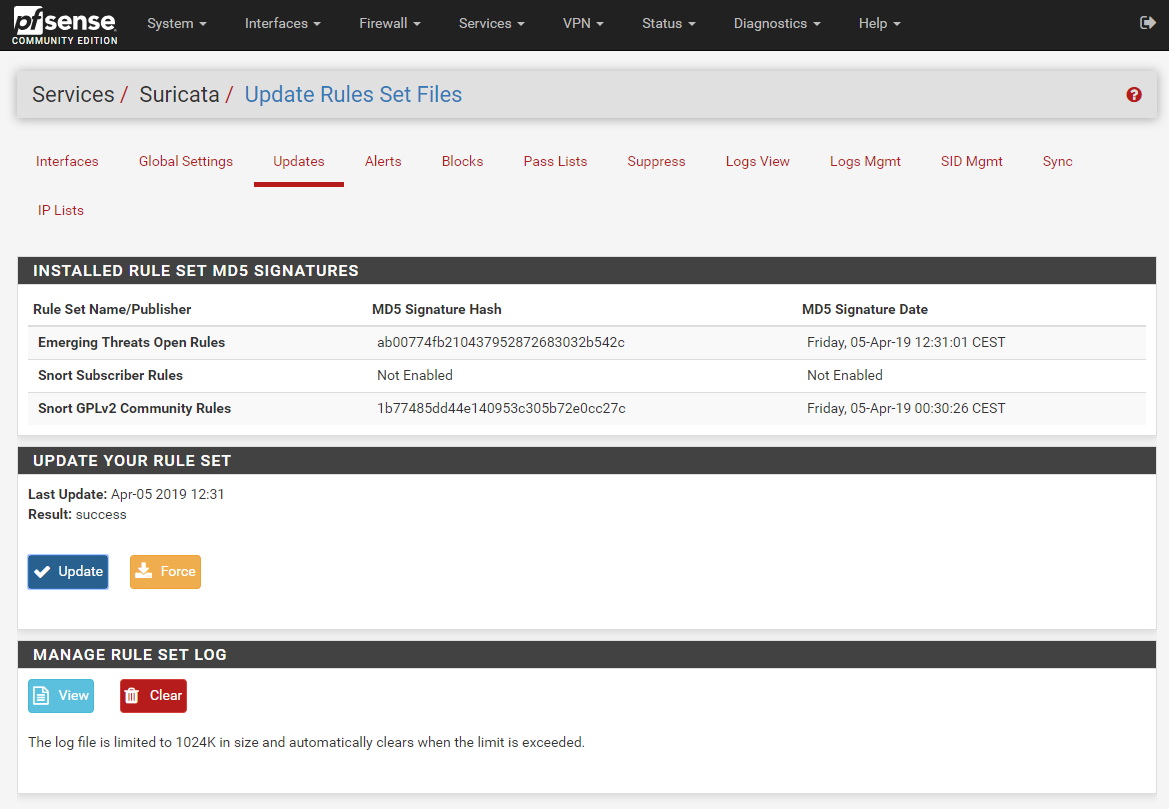
I have used the Snort community rules and the Emerging threats rules these are both free to use and do a decent job of protecting the network with not too many false positives.
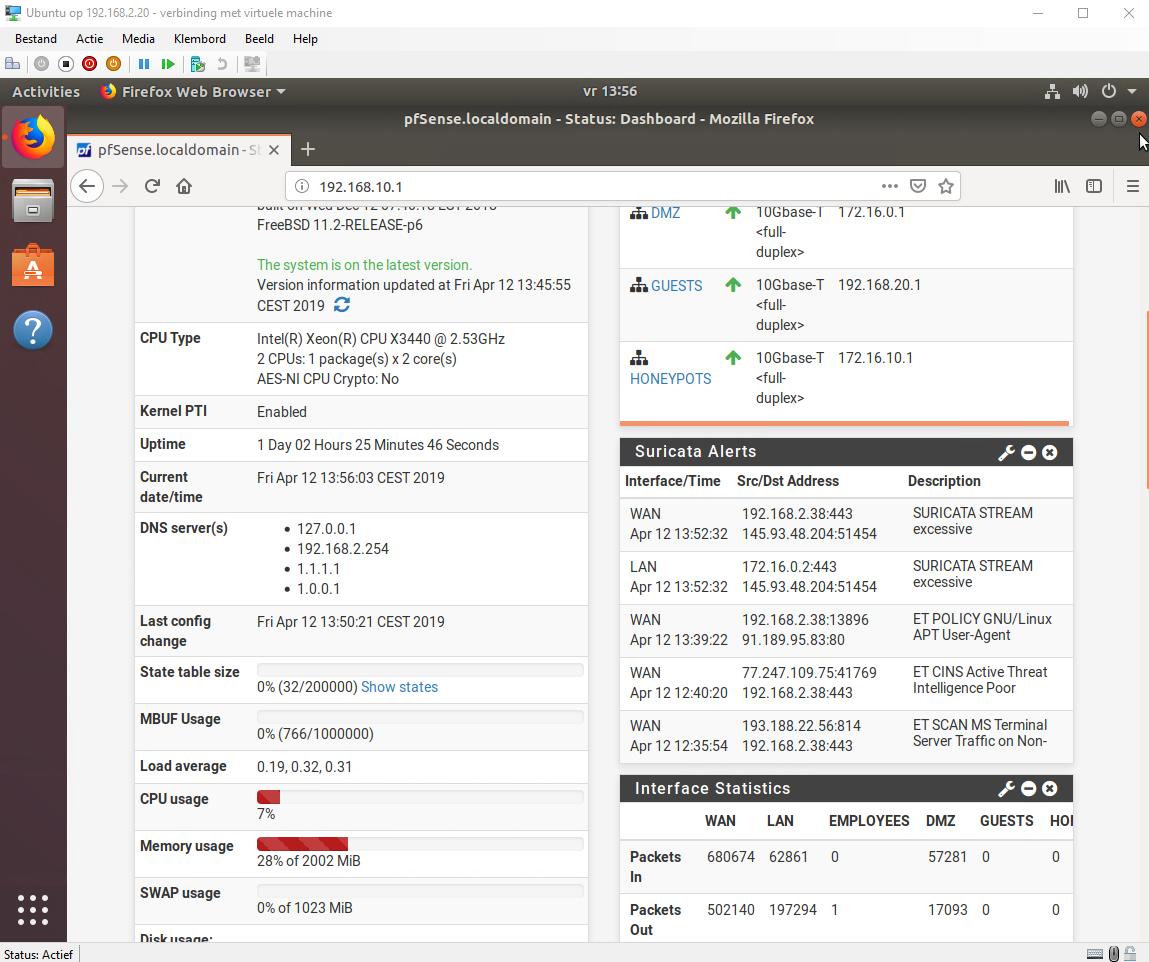
We encountered a real world scenario which actually turned out to work really well with an IPS. Bram tried to DDOS my website while it was running in my pfsense environment. The IPS immediately noticed this and blocked his IP. While the website was running outside the pfsense zone Bram could DDOS all he want without getting blocked.
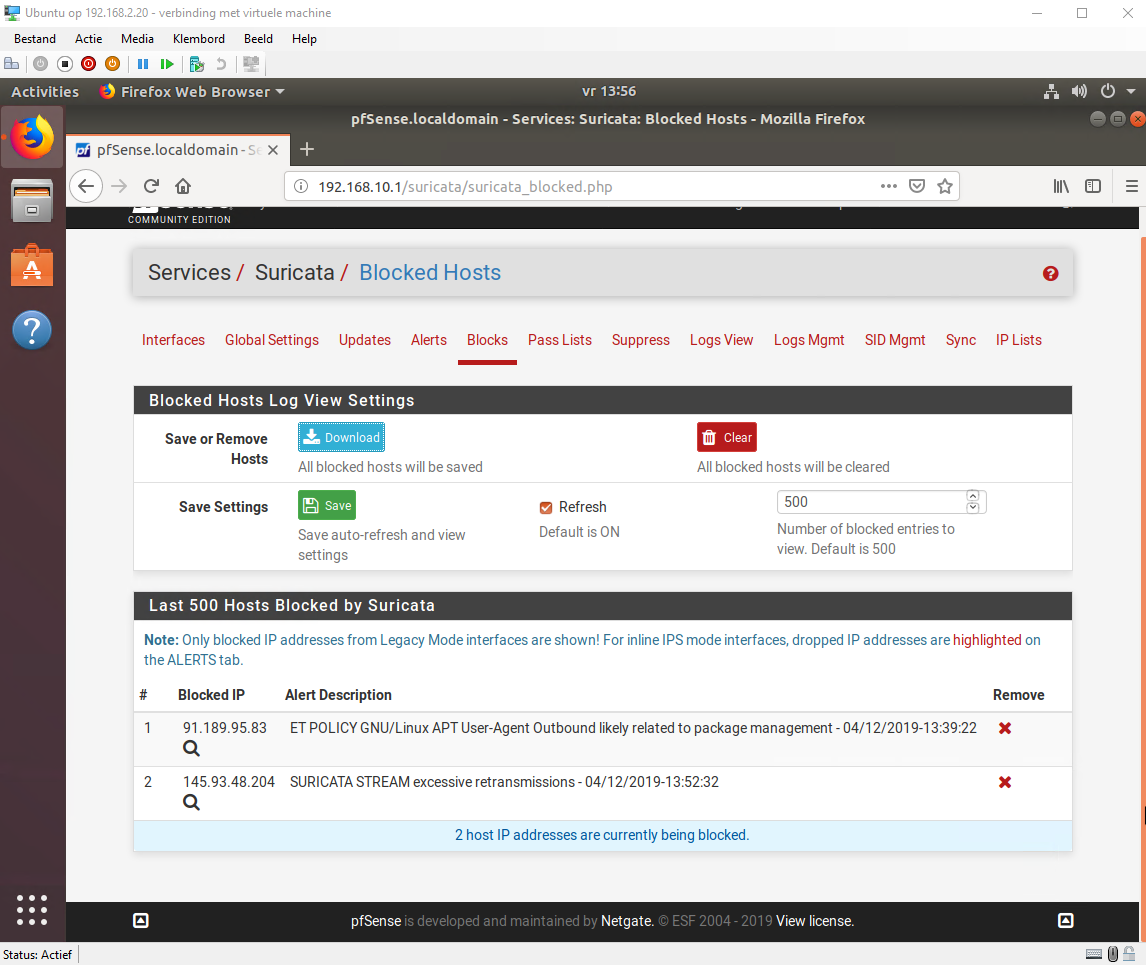
Here you can see Bram's IP in the Suricata blocklist.
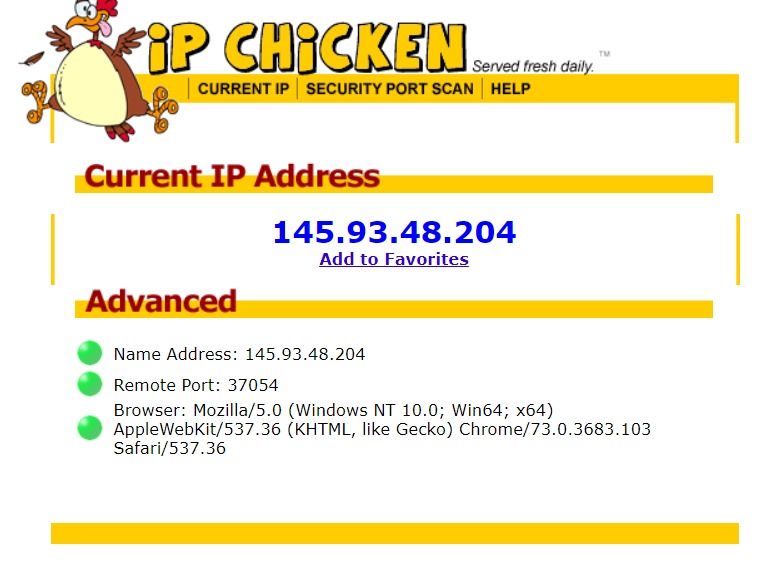
This is a screenshot from Bram's computer with his IP he used for generating the alert.
- Date: April 2019
- Client: Fontys
- Category: IDS/IPS